You might’ve already heard of phishing, primarily in the term of “voice phishing”, but the term “phishing” has a broader sense in itself. Phishing isn’t entirely a new attack; it has been around since the mid-1990s. Nevertheless, many people may still be unaware of how to defend themselves against being “phished”. The word “phishing” is created by combining two words: “phreaking ” and “fishing,” as attackers attempt to “fish” users in various ways to gain access to sensitive information. This article will specifically focus on phishing through Email.
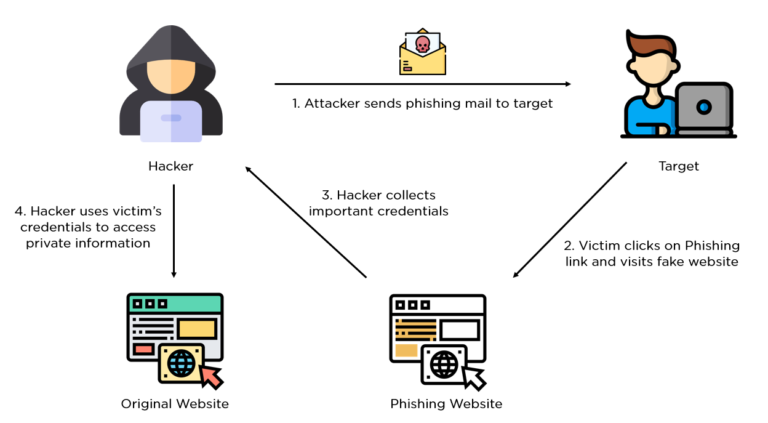
There are various ways that attackers use to trick users into giving their valuable information, and phishing through email is one of the most common ways. The image shown below showcases it.
There are a few ways that an attacker might do this, but the attack would look something like getting an email from a big corporation that you are probably logged into. The email would appear legitimate, and it would request your login credentials, claiming that you need to re-login due to a security measure or a promotional offer they are running. (This tactic in phishing or any other cyber attack, where attackers would try to gain your trust, in hopes of you letting your guard down, is called social engineering.) Then the users would fill in their information, which would be delivered right to the attacker. On a bit unrelated note, you might not think that the attacks are catastrophic, thinking that you could just change your password and notify the real corporation that your account has been breached, as in most cases, they would reset your password for you. However, the truth is that most people use the same passwords on multiple platforms and don’t bother to add a two-factor system, meaning that attackers would try to brute-force their way in for your other accounts on different platforms with the same password, and again, in most cases, it works.
The reason why so many people can or have faced email phishing is that it has become so easy for the attackers to automate the process and spam it to you and others in large quantities. As the phishing attacks advanced, it became more difficult to easily identify them. More advanced phishing attacks through email would actually have a link or a malicious link that would look like something you would find in a legitimate company.
One of the easiest ways to identify phishing is by checking the sender’s address, as the sender’s email address should be from that corresponding company. However, attackers have figured out how to trick, like this: “@microsoft” “@rnicrosoft”, these addresses look identical, especially from afar, but if you check closely, that one in the last tried to mimic the “m” by using “rn”. So you might think that you wouldn’t be falling for this trick, but the attacker figured out that they can use special letters or letters from other than English that look exactly like an existing letter. So, although many phishing attacks can be filtered out this way, identifying phishing attacks is definitely not foolproof.
Example image of this:
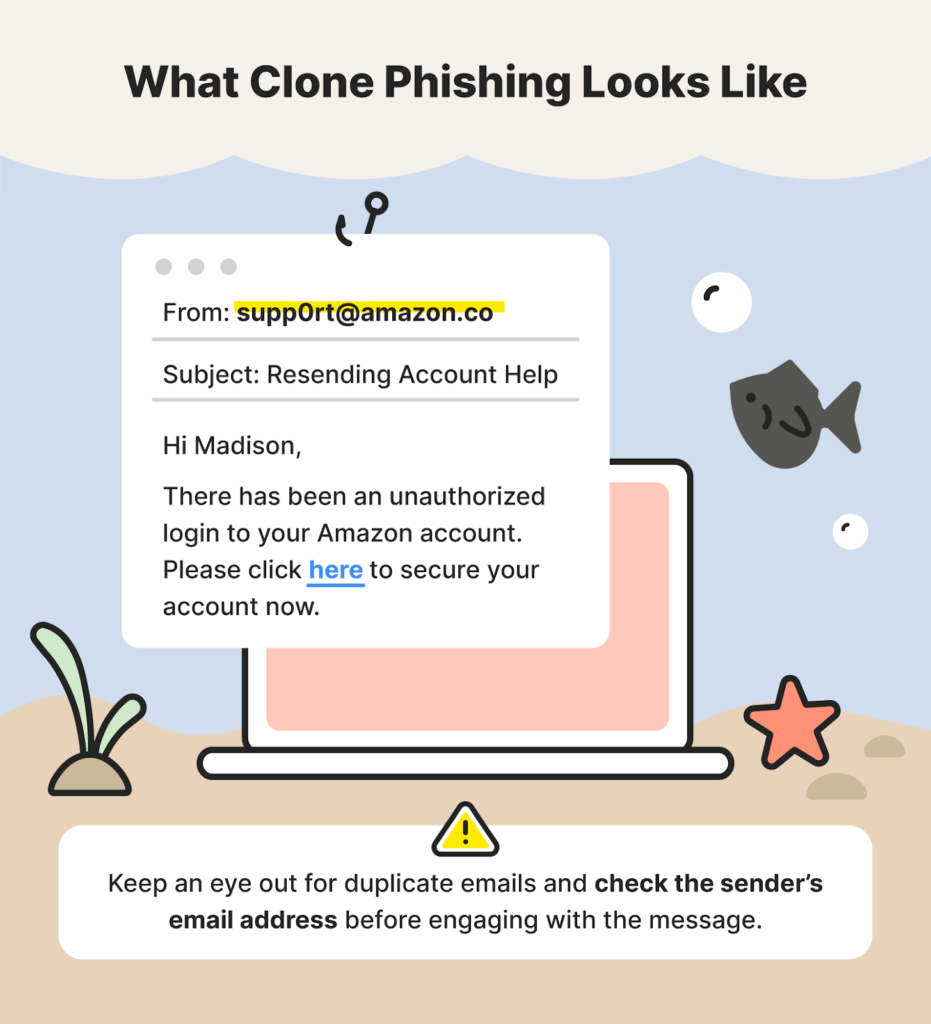
https://us.norton.com/blog/online-scams/types-of-phishing
So, how do we not get phished? Thankfully, there are quite a few ways, but some of the easier ways that let you differentiate them are by sending an email to the legitimate company’s email address regarding the email they “supposedly” sent. This way, you can check with the actual source and confirm whether it is legitimate mail. This method, although a bit time-consuming, is always better than exposing your sensitive credentials, especially in banking.
Moreover, if the suspicious email you suspect is a phishing link or a malicious link, do not click it, do not get curious, although a handful of sites look legitimate and are not blocked, for more advanced phishing, even clicking on the site could spoof your other sensitive information and sell it on databases. Instead, go to a website called “VirusTotal” and insert the site’s link; although not foolproof, it can flag out common spyware or any other viruses for that site that would try to juice your data.
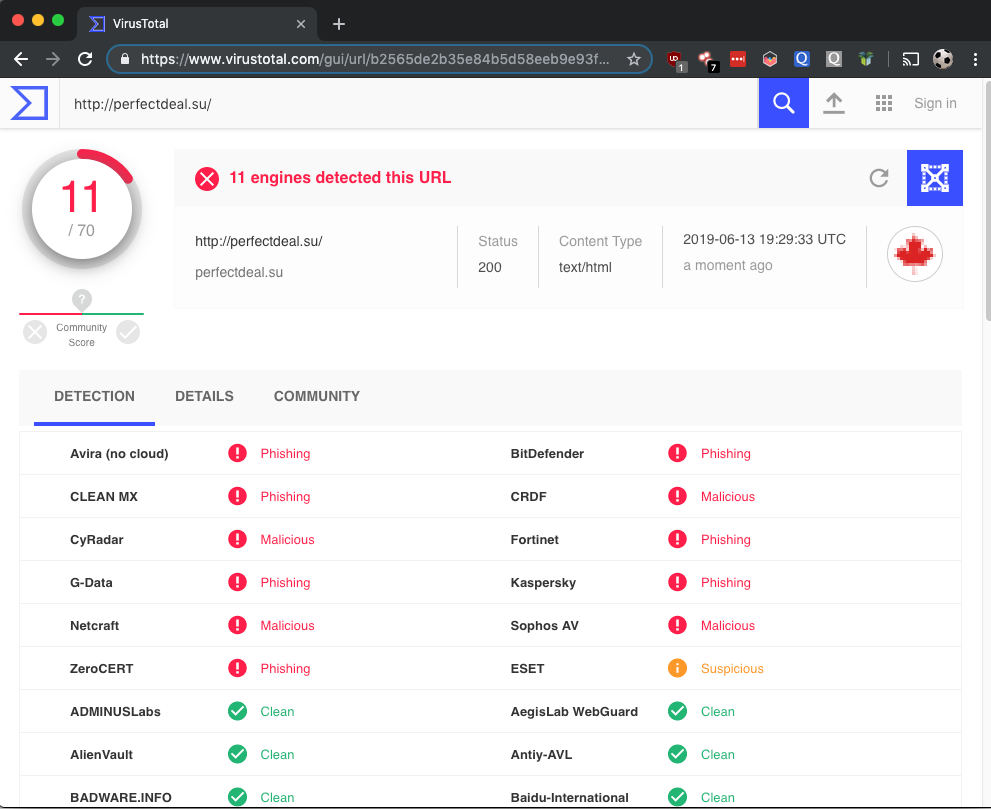
(https://medium.com/maverislabs/virustotal-is-not-an-incident-responder-80a6bb687eb9)
In conclusion, as phishing tactic advances more and more, it is important to know how to keep yourself safe from these attacks, and primary two examples of how to confirm whether if the sender is legitimate or try to exploit you are: checking their authenticity by checking up with the actual corporation respectively and not clicking on suspicious links, not even for your curiosity. And last but not least, use your common sense and don’t click on stuff that sounds desperate, absurd, or sounds too good to be true.
By. Geumchang An
Phishing Attacks Through Email: What They Are and How to Avoid Them
You might’ve already heard of phishing, primarily in the term of “voice phishing”, but the term “phishing” has a broader sense in itself. Phishing isn’t entirely a new attack; it has been around since the mid-1990s. Nevertheless, many people may still be unaware of how to defend themselves against being “phished”. The word “phishing” is created by combining two words: “phreaking ” and “fishing,” as attackers attempt to “fish” users in various ways to gain access to sensitive information. This article will specifically focus on phishing through Email.
There are various ways that attackers use to trick users into giving their valuable information, and phishing through email is one of the most common ways. The image shown below showcases it.
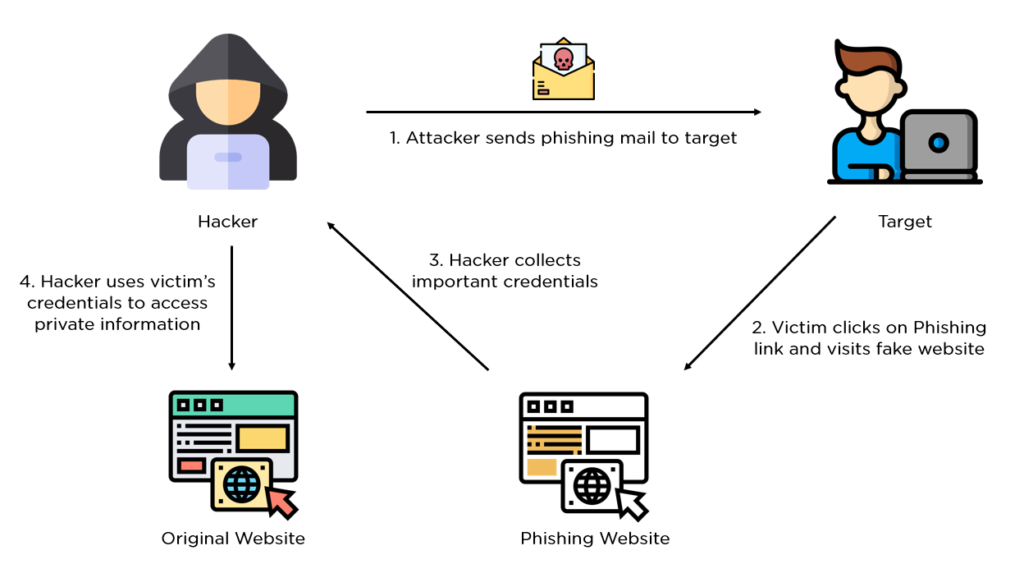
(https://www.simplilearn.com/tutorials/cryptography-tutorial/what-is-phishing-attack)
There are a few ways that an attacker might do this, but the attack would look something like getting an email from a big corporation that you are probably logged into. The email would appear legitimate, and it would request your login credentials, claiming that you need to re-login due to a security measure or a promotional offer they are running. (This tactic in phishing or any other cyber attack, where attackers would try to gain your trust, in hopes of you letting your guard down, is called social engineering.) Then the users would fill in their information, which would be delivered right to the attacker. On a bit unrelated note, you might not think that the attacks are catastrophic, thinking that you could just change your password and notify the real corporation that your account has been breached, as in most cases, they would reset your password for you. However, the truth is that most people use the same passwords on multiple platforms and don’t bother to add a two-factor system, meaning that attackers would try to brute-force their way in for your other accounts on different platforms with the same password, and again, in most cases, it works.
The reason why so many people can or have faced email phishing is that it has become so easy for the attackers to automate the process and spam it to you and others in large quantities. As the phishing attacks advanced, it became more difficult to easily identify them. More advanced phishing attacks through email would actually have a link or a malicious link that would look like something you would find in a legitimate company.
One of the easiest ways to identify phishing is by checking the sender’s address, as the sender’s email address should be from that corresponding company. However, attackers have figured out how to trick, like this: “@microsoft” “@rnicrosoft”, these addresses look identical, especially from afar, but if you check closely, that one in the last tried to mimic the “m” by using “rn”. So you might think that you wouldn’t be falling for this trick, but the attacker figured out that they can use special letters or letters from other than English that look exactly like an existing letter. So, although many phishing attacks can be filtered out this way, identifying phishing attacks is definitely not foolproof.
Example image of this:
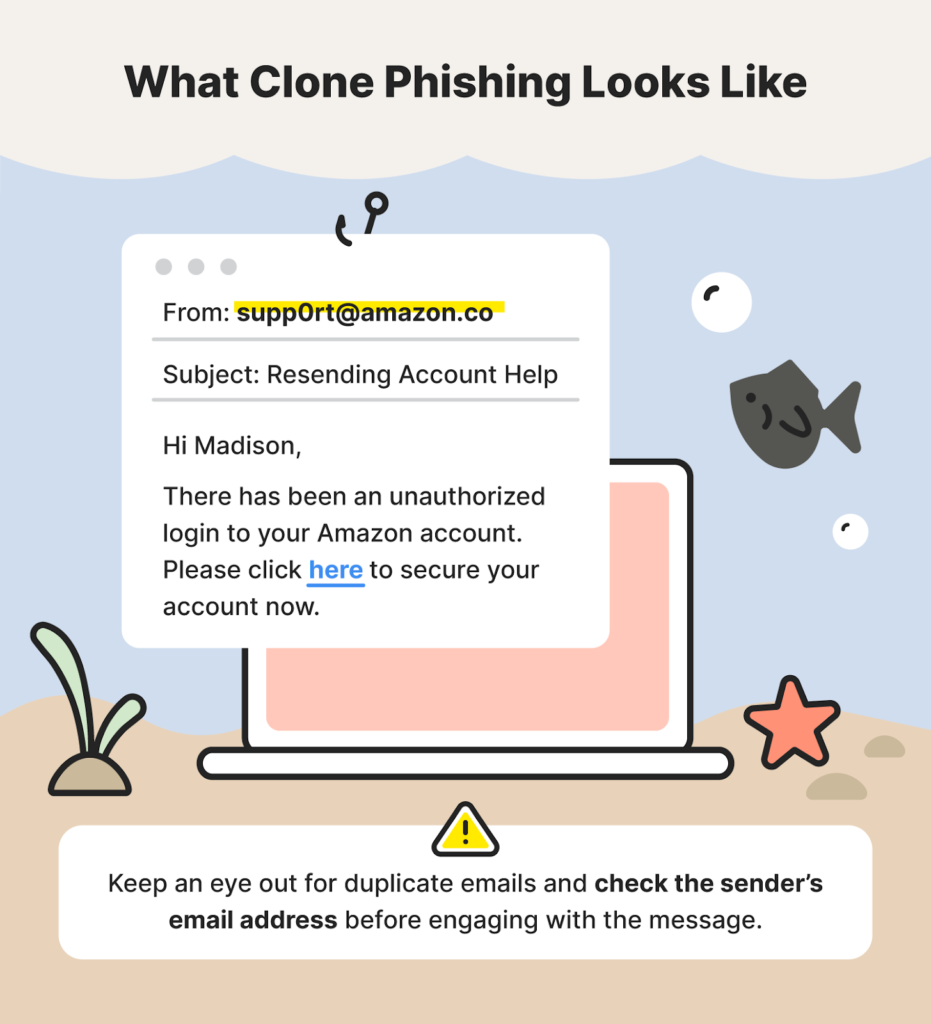
https://us.norton.com/blog/online-scams/types-of-phishing
So, how do we not get phished? Thankfully, there are quite a few ways, but some of the easier ways that let you differentiate them are by sending an email to the legitimate company’s email address regarding the email they “supposedly” sent. This way, you can check with the actual source and confirm whether it is legitimate mail. This method, although a bit time-consuming, is always better than exposing your sensitive credentials, especially in banking.
Moreover, if the suspicious email you suspect is a phishing link or a malicious link, do not click it, do not get curious, although a handful of sites look legitimate and are not blocked, for more advanced phishing, even clicking on the site could spoof your other sensitive information and sell it on databases. Instead, go to a website called “VirusTotal” and insert the site’s link; although not foolproof, it can flag out common spyware or any other viruses for that site that would try to juice your data.
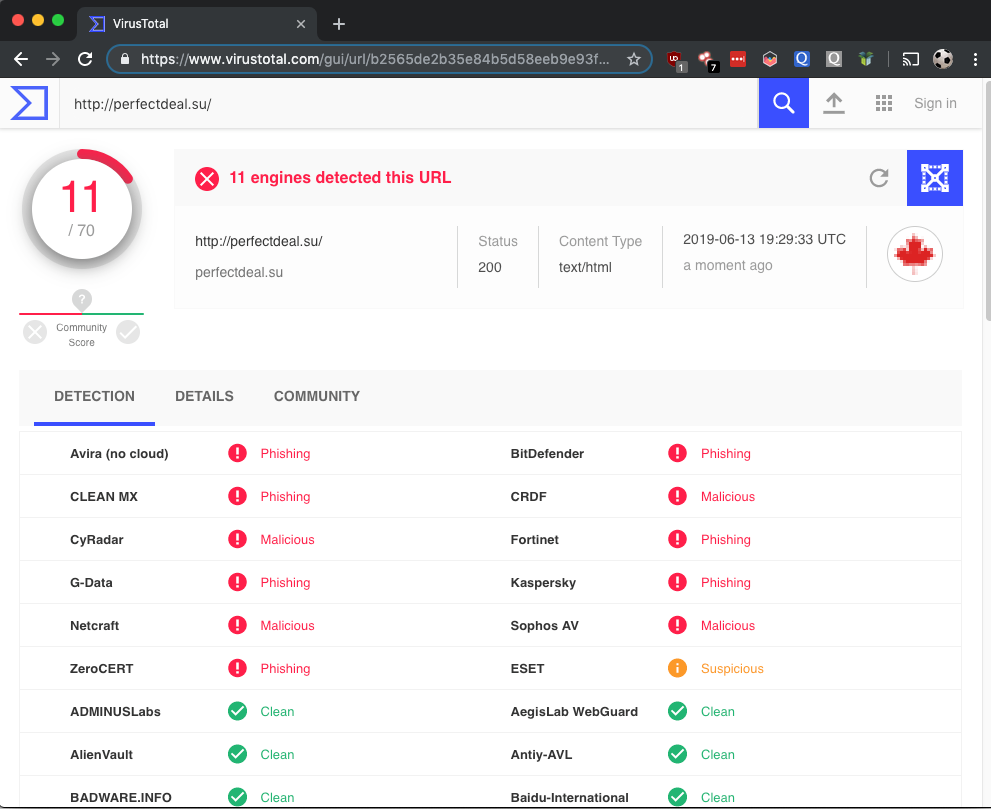
(https://medium.com/maverislabs/virustotal-is-not-an-incident-responder-80a6bb687eb9)
In conclusion, as phishing tactic advances more and more, it is important to know how to keep yourself safe from these attacks, and primary two examples of how to confirm whether if the sender is legitimate or try to exploit you are: checking their authenticity by checking up with the actual corporation respectively and not clicking on suspicious links, not even for your curiosity. And last but not least, use your common sense and don’t click on stuff that sounds desperate, absurd, or sounds too good to be true.
By. Geumchang An
Works Cited
Cloudflare, https://www.cloudflare.com/learning/access-management/phishing-attack/.Accessed
27 Oct. 2025.