Web vulnerabilities are a weakness or misconfiguration in the design of a website that can be exploited by attackers to compromise its integrity and availability (by DDoS attack), or the confidentiality of its users. There are many different kinds of vulnerabilities a site could have, and some of the most common vulnerabilities are: being vulnerable to SQL, having a broken authentication system, and giving out sensitive data to other clients.
- Injection Attacks (SQL):
Many websites are based on SQL(Structured Query Language) format, as it is the standard programming language used to interact with and manage data in databases. It allows users to store, retrieve, and update data, enabling both users and the site owner to manage data efficiently. If a website is vulnerable to SQL, attackers could inject malicious SQL code directly to the site without permission or knowledge of the owner of the site to manipulate the website’s database. A well-made website shouldn’t be vulnerable to SQLi attacks, as SQLi attacks happen by exploiting small details that might’ve been overlooked while creating the site.
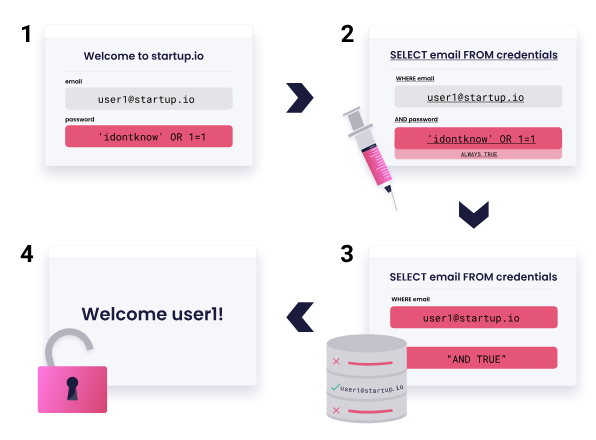
This photo very roughly demonstrates how SQLi works. By modifying the query’s logic, the query will evaluate as “true” even though the provided password is invalid. Since if the query decides whether the user can be logged in, by doing so, one could exploit this vulnerability by injecting malicious code, and by manipulating the string on the websites.
SQL injection attacks can lead to various detrimental consequences, such as data breaches, data corruption, or the owner losing access to the website.
- Broken Authentication System Vulnerability:
If a site has a weak authentication mechanism, it can lead to broken authentication vulnerabilities. Attackers exploit these weaknesses to gain unauthorized access to other users’ accounts and sensitive information by logging into others’ accounts. A proper and secure site should be able to protect its users’ accounts and ensure that no one else can access it without their confirmation. Sites should double-check with the original account if another one is trying to log in on a different server or on different devices. Sites should also make sure that the passwords the user sets are strong enough, such as setting the required number of characters for the password. However, these vulnerabilities aren’t entirely the sites’ fault, as we, the users, should use common sense and set a strong password that doesn’t repeat across different sites, and add a 2FA(two-factor authentication system), as many applications nowadays offer it.
- Exposure of Sensitive Data:
Websites may unintentionally expose sensitive information, such as user credentials, payment details, or users’ sensitive data, due to a misconfiguration or flaw in the code of the website. Attackers can find these vulnerabilities through insecure storage or databases, or negligence in handling sensitive information of users and the site itself. After identifying the vulnerability, attackers could not only look into other clients’ or users’ data, or even worse, gain unauthorized access to the site and remove any other access from the original owner of the site.
A major leak occurred in 2021, as the Microsoft Power Apps Portals site contained millions of sensitive data points. The site inadvertently made its users’ data accessible to everyone, exposing their employees’ personal information to the public.
The picture below shows the actual leak of approximately 38 million victims who were affected by Microsoft’s carelessness, and thus the result of the exposure of sensitive data.
(https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgQWZdwH9UK67sNk05vBCHpwfk1LnX2zlTkLvdWfFm-37acQcNanKlhdiXy7PY31QgA7CQ6HPRC2TQYvTJWHRkZOySgpEkI7e9sUbWXJG0ZuL9EzgA2Nj9W5LjHsqenim2kOgUV9YKUMVo/s0/data-leak.jpg)
All three major types of website vulnerabilities have one thing in common, and it is that they are caused by misconfiguration in the code of the website. Attacker manipulates and makes the code of the website trust it into giving unauthorized “admin” control in the site, or secreting “snooping” sensitive information from other users.
This is the reason why you can’t always blindly trust a site; giving your sensitive information and credentials to websites that are full of vulnerabilities could cause serious damage. Even well-known websites aren’t bulletproof, as there are multiple instances where attackers manipulate and exploit these vulnerabilities of websites, and leak data in the databases.
The bottom line is that you shouldn’t be trusting every site you visit and give out your sensitive data, not because of their authenticity and their intentions, but rather because of the weak security features that might have, consequently leading to your data being leaked or stolen. You should always try to question their integrity, their intention with your data, and, more importantly, you should check if they have had any major data leaks in the past. Many companies, however, especially smaller ones, try to cover up their data leaks and misconfigurations.
By. Geumchang An
Works Cited
Chinnasamy, Vinugayathri. “Understanding Website Vulnerabilities: Exploitation and
Prevention.” Indusface, 23 Mar. 2024,
https://www.indusface.com/blog/what-is-a-website-vulnerability-and-how-can-it-be-exploited/
Pryimenko, Liudmyla. “7 Examples of Real-Life Data Breaches Caused by Unmitigated Insider
Threats.” Syteca, 17 Dec. 2025,
https://www.syteca.com/en/blog/real-life-examples-insider-threat-caused-breaches